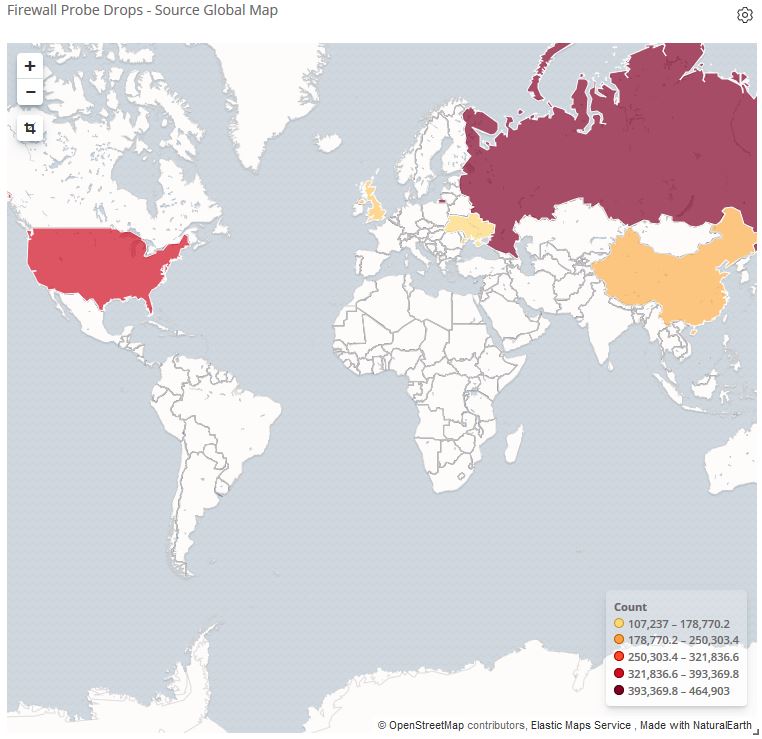
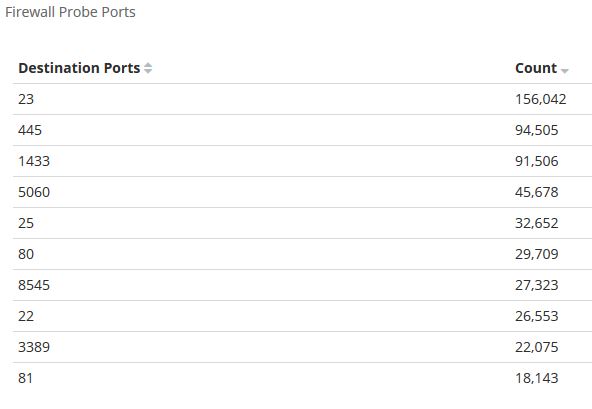
The top question among IT professionals is always this:
How prepared are we during an outage or data loss?
The typical follow up questions would be:
- What are the root causes?
- How do we recover?
- How do we prevent it from happening again?
- What is the cost of the damage?
The Ponemon Institute study (2016) showed the most common cause of outages are UPS power failure, cyber crime, and human error. If the research is conducted now (2019), cyber crime will probably be on top – as seen from today’s headlines with many banks and corporations (including manufacturing sector) hacked and data breached. The report also indicates this, as the trend jumped from 2% in 2010 to 22% in 2016!
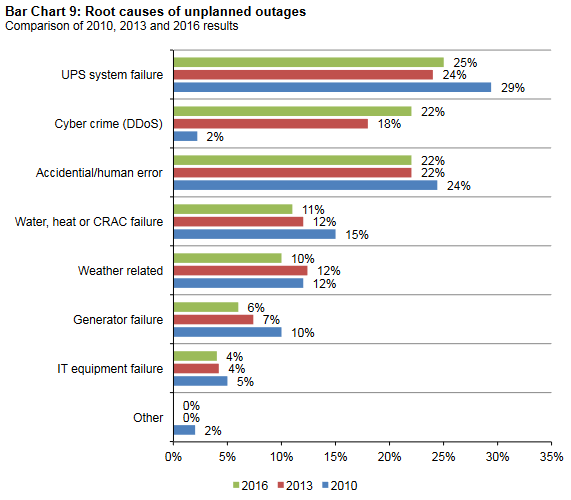
Root Causes of Unplanned Outages
Preparation for inevitable disasters will certainly involve more investment in cyber security training and update outdated software and hardware. It also helps to keep things simple, and not introduce unproven technology just for the sake of being trendy, or on the “bleeding edge”.
It is easier said than done. However, it’s not impossible. Management needs to be more aware that complicated business process introduce more human errors. Introducing many systems can also expose many weaknesses when IT teams tries to connect them together, to share data. Having multiple sites outside a traditional Enterprise data center also exposes data to be breached either by external hacker, or internal leak.
Prevention is certainly the priority for many concerned IT experts. Knowing the common points of failures, additional checks and balances in data recovery services and stressing security concerns for the employees are important first steps. One can’t simply wait for the storm to come. Instead, prepare for the storm and budget accordingly.